In the digital age, where cyber threats are more prevalent than ever, safeguarding your online accounts is of paramount importance. One effective way to enhance your security is through 2f authentication, also known as two-factor authentication. This security measure adds an extra layer of protection by requiring a second form of verification before granting access to your accounts. By implementing 2f authentication, you can significantly reduce the risk of unauthorized access and fortify your digital defenses.
As technology advances, so do the tactics of cybercriminals. With the rise of sophisticated hacking techniques, it is crucial for individuals and businesses alike to adopt robust security measures. 2f authentication is a powerful tool in the fight against cyber threats, providing an additional safeguard beyond just a username and password. Whether it's for personal accounts or sensitive business data, integrating 2f authentication can be a game-changer in ensuring your information remains secure.
In this article, we will delve into the intricacies of 2f authentication, exploring its benefits, implementation methods, and the impact it can have on your digital security. From understanding the basics to unraveling the complexities, we'll provide you with a comprehensive guide to making the most of this essential security feature. So, buckle up as we embark on a journey to secure your digital world with the power of 2f authentication.
Read also:Unveil The Oasis Discover Dry Town Water Park In Palmdale
Table of Contents
- What is 2f Authentication?
- The Importance of 2f Authentication
- How Does 2f Authentication Work?
- Types of 2f Authentication
- Benefits of Using 2f Authentication
- How to Implement 2f Authentication?
- Common Challenges with 2f Authentication
- Overcoming 2f Authentication Challenges
- 2f Authentication in Business
- Future of 2f Authentication
- Is 2f Authentication Foolproof?
- Real-Life Examples of 2f Authentication
- Integration with Other Security Measures
- Frequently Asked Questions
- Conclusion
What is 2f Authentication?
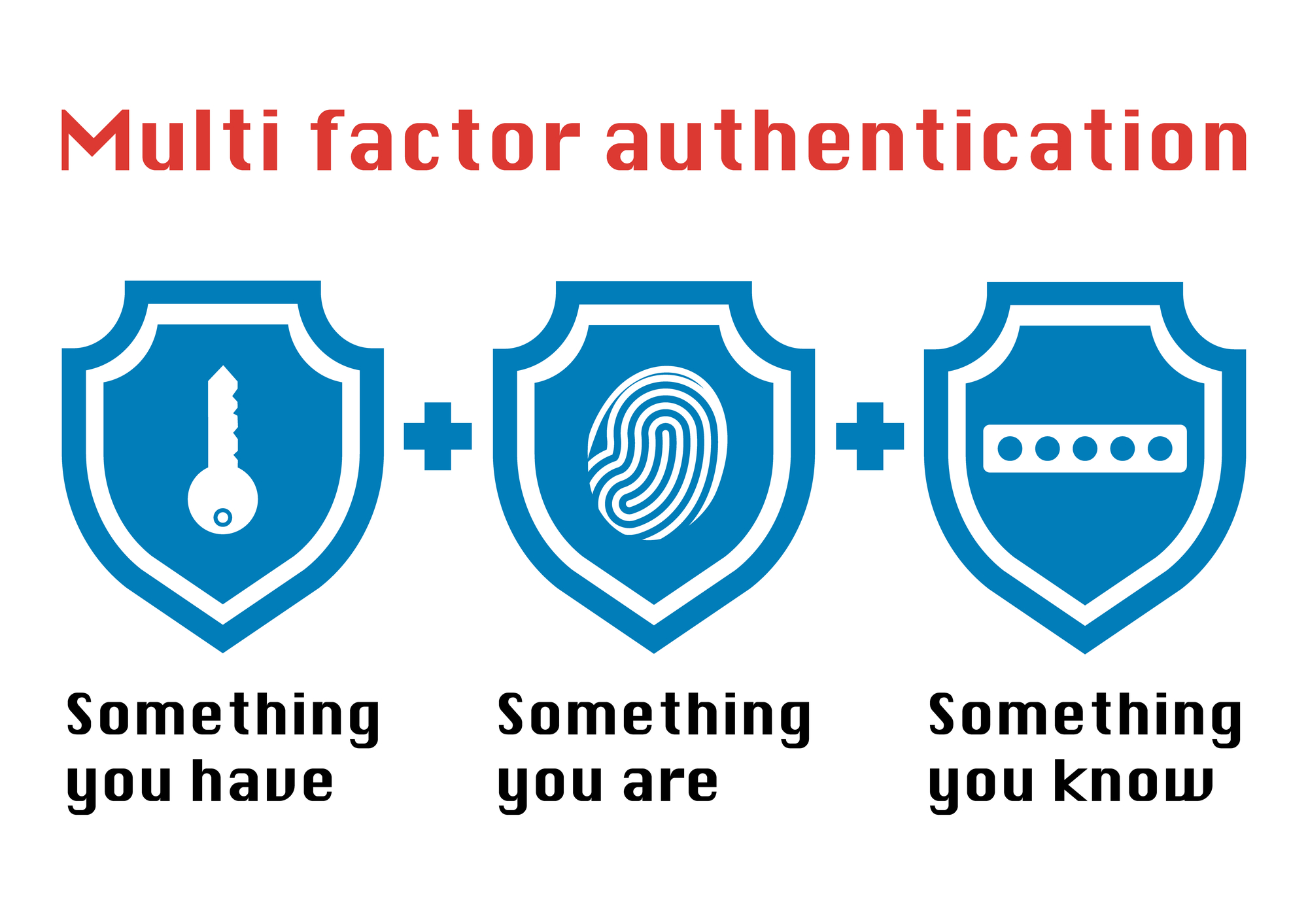
2f authentication, or two-factor authentication, is a security process that requires two different authentication factors to verify a user’s identity. This extra layer of security ensures that the person trying to gain access is truly who they say they are. The two factors involved are typically something you know (like a password) and something you have (like a smartphone).
The Importance of 2f Authentication
In today's world, cyber threats are constantly evolving, making it crucial to implement security measures that can keep up with these changes. 2f authentication is important because it:
- Provides an additional layer of security beyond passwords
- Reduces the risk of unauthorized access
- Protects sensitive information from being compromised
- Enhances user confidence in digital transactions
How Does 2f Authentication Work?
The process of 2f authentication typically involves the following steps:
- User enters their username and password.
- The system sends a verification code to the user’s registered device.
- User enters the verification code to gain access.
This method ensures that even if a password is compromised, unauthorized users cannot access the account without the second factor.
Types of 2f Authentication
There are various types of 2f authentication methods available, including:
- SMS-based Authentication: A code is sent to your mobile phone via SMS.
- Email-based Authentication: A code is sent to your registered email address.
- App-based Authentication: An authentication app generates a code.
- Hardware Tokens: Physical devices that generate authentication codes.
- Biometric Authentication: Uses fingerprint or facial recognition.
Benefits of Using 2f Authentication
The adoption of 2f authentication brings multiple benefits, such as:
Read also:A Guide To Claremont Your Destination For Culture And Charm
- Enhanced security for online accounts
- Reduced risk of identity theft
- Protection against phishing attacks
- Increased user trust and confidence
How to Implement 2f Authentication?
Implementing 2f authentication involves several steps:
- Choose the type of 2f authentication suitable for your needs.
- Ensure your accounts support 2f authentication.
- Follow the service provider's instructions to enable the feature.
- Test the implementation to ensure it functions correctly.
Common Challenges with 2f Authentication
While 2f authentication is effective, users may encounter certain challenges, such as:
- Loss of access to the second factor (e.g., losing a device)
- Technical issues with authentication apps
- Inconvenience during login processes
Overcoming 2f Authentication Challenges
To mitigate these challenges, consider the following solutions:
- Keep backup codes in a secure location.
- Ensure devices are up to date and functioning.
- Enable multiple authentication methods.
2f Authentication in Business
Businesses can greatly benefit from 2f authentication by implementing it to:
- Protect sensitive corporate data
- Enhance customer trust
- Comply with security regulations
Deploying 2f authentication in a business environment requires careful planning and execution to ensure smooth operations.
Future of 2f Authentication
The future of 2f authentication looks promising, with advancements in technology paving the way for more secure and user-friendly solutions. Innovations such as biometric verification and machine learning are expected to enhance the reliability and effectiveness of 2f authentication systems.
Is 2f Authentication Foolproof?
While 2f authentication significantly enhances security, it is not entirely foolproof. Attackers may still find ways to bypass this security measure. However, when combined with other security practices, 2f authentication remains a formidable barrier against unauthorized access.
Real-Life Examples of 2f Authentication
Many well-known companies have successfully implemented 2f authentication, including:
- Google: Offers 2f authentication for Google accounts via SMS, app, or hardware keys.
- Apple: Implements 2f authentication for Apple ID accounts, using trusted devices or numbers.
- Microsoft: Provides 2f authentication for Microsoft accounts through apps or phone calls.
Integration with Other Security Measures
For optimal security, 2f authentication should be integrated with other measures like:
- Regular password updates
- Firewall and antivirus protection
- Security awareness training
Frequently Asked Questions
What is the main purpose of 2f authentication?
The primary purpose of 2f authentication is to provide an additional layer of security by requiring two forms of verification, thereby reducing the risk of unauthorized account access.
Can 2f authentication be bypassed?
While 2f authentication enhances security, it is not entirely infallible. Attackers might exploit vulnerabilities, but combining it with other security measures can significantly reduce risks.
What types of 2f authentication are most secure?
Biometric methods, such as fingerprint or facial recognition, are considered highly secure due to their reliance on unique physical characteristics that are difficult to replicate.
How does 2f authentication improve business security?
By implementing 2f authentication, businesses can protect sensitive data, ensure compliance with regulations, and build trust with customers by demonstrating a commitment to security.
Is 2f authentication user-friendly?
While it adds an extra step to the login process, many users find 2f authentication to be a minor inconvenience compared to the significant security benefits it offers.
What should I do if I lose access to my second factor?
If you lose access to your second factor, use backup codes provided during setup, or contact the service provider for assistance in regaining access.
Conclusion
In conclusion, 2f authentication is an essential security measure in the modern digital landscape. By requiring two forms of verification, it significantly enhances the security of online accounts, protecting against unauthorized access and cyber threats. While it is not entirely foolproof, when used in conjunction with other security practices, 2f authentication remains a highly effective tool for safeguarding personal and business data.
For further reading on enhancing online security, visit Cybersecurity Guide.