In today's digital age, API keys have become an essential element in the realm of secure communication between applications. These seemingly simple strings of alphanumeric characters serve a critical purpose in the authentication and authorization process, ensuring that only permitted applications gain access to specific data or services. In essence, API keys act as a gatekeeper, safeguarding sensitive information from unauthorized access while facilitating seamless interaction between different software systems. As technology continues to evolve, understanding the function and significance of API keys is crucial for developers and businesses alike.
API keys are not just a tool for security; they are a means of providing structure and control over how data is accessed and manipulated. They enable developers to implement fine-grained access controls, allowing for tailored access based on the needs of the application. This flexibility ensures that applications can interact with APIs in a manner that aligns with the business logic and security requirements of the organization. Additionally, API keys can be used to monitor usage patterns, providing valuable insights into how and when APIs are being utilized, which can inform future development and optimization strategies.
The importance of API keys extends beyond just security and access control. They play a pivotal role in the monetization strategies of many businesses, particularly those offering software as a service (SaaS) or platform as a service (PaaS) solutions. By controlling access to their APIs through keys, companies can implement pricing models based on usage, offering different tiers of service based on the level of access granted. This not only provides a revenue stream but also ensures that resources are allocated efficiently, preventing abuse and overuse of the system. As the digital landscape continues to expand, the role of API keys will only grow in importance, making them a critical component of modern software development.
Read also:Discover The Ultimate Patos Pelivula Mega Movie Experience
Table of Contents
- Introduction to API Keys
- Why Are API Keys Important?
- How Do API Keys Work?
- The Structure of API Keys
- How Are API Keys Used in Authentication?
- What Are the Security Benefits of API Keys?
- Implementing API Keys in Your Application
- What Are the Best Practices for Managing API Keys?
- Common Challenges with API Keys
- How to Securely Store API Keys?
- API Keys vs. OAuth Tokens: What's the Difference?
- What Are the Limitations of API Keys?
- Future Trends in API Key Management
- Frequently Asked Questions About API Keys
- Conclusion: The Ongoing Role of API Keys
Introduction to API Keys
API keys are an integral part of modern software development. They provide a method for authenticating requests to an API, ensuring that only authorized users or applications can access the resources provided by the API. This makes them a crucial component in protecting sensitive data and maintaining the integrity of a software system.
API keys are typically used in web applications, mobile apps, and cloud services to control access to APIs. They are often issued by the API provider and must be included in the request header or as a query parameter when making API calls. This allows the provider to track and monitor usage, enforce rate limits, and prevent unauthorized access.
The use of API keys has become increasingly popular as the demand for third-party integrations and cloud-based services has grown. They offer a simple and effective way to secure APIs while providing developers with the flexibility to build powerful, interconnected applications.
Why Are API Keys Important?
API keys play a critical role in the security and functionality of modern applications. They serve as a means of identifying and authenticating users or applications that are accessing an API. This ensures that only authorized parties can access the resources provided by the API, protecting sensitive data from unauthorized access.
In addition to security, API keys are also important for monitoring and controlling usage. By requiring API keys for access, developers can track how often an API is being used, by whom, and in what context. This information can help identify trends, optimize performance, and plan for future development.
Furthermore, API keys enable developers to implement access controls, allowing them to specify which resources or services a particular key can access. This provides a granular level of control over how APIs are used, ensuring that applications can only perform actions that align with the business logic and security requirements of the organization.
Read also:Explore Every Nook And Cranny Uncover Hidden Gems And Secrets
How Do API Keys Work?
API keys are typically generated by the API provider and issued to developers who wish to use the API. They are unique to each application or user and must be included in the request header or as a query parameter when making API calls.
When a request is made to an API with an API key, the provider checks the key against a database of valid keys. If the key is valid, the request is processed and access to the requested resources is granted. If the key is invalid or missing, the request is denied, and an error message is returned.
This process ensures that only authorized applications or users can access the API, protecting sensitive data and resources from unauthorized access. It also allows the provider to monitor usage, enforce rate limits, and track who is using the API and how often.
The Structure of API Keys
API keys are typically alphanumeric strings that are generated by the API provider. They are often designed to be unique and difficult to guess, ensuring that unauthorized parties cannot easily gain access to the API.
The structure of an API key can vary depending on the provider, but they generally consist of a combination of letters and numbers. Some providers may also include special characters or use a specific format, such as a UUID or a hash, to enhance security.
In addition to the key itself, API providers may also include metadata or additional information, such as expiration dates or usage limits, to help manage and control access to the API.
What Makes an API Key Secure?
To ensure the security of an API key, it is important to follow best practices for generating and managing keys. This includes using strong, unique keys that are difficult to guess and regularly rotating keys to minimize the risk of unauthorized access.
Additionally, API keys should be stored securely and never exposed in client-side code or publicly accessible locations. This helps prevent unauthorized parties from gaining access to the key and using it to access the API.
How Are API Keys Used in Authentication?
API keys are a common method of authentication for APIs, providing a simple and effective way to verify the identity of a user or application. They are typically included in the request header or as a query parameter when making API calls, allowing the provider to verify the key and grant access to the requested resources.
In addition to authentication, API keys can also be used to implement access controls, allowing developers to specify which resources or services a particular key can access. This provides a granular level of control over how APIs are used, ensuring that applications can only perform actions that align with the business logic and security requirements of the organization.
What Are the Different Types of API Authentication?
- API Keys: A simple method of authentication that requires a unique key to access the API.
- OAuth: A more complex authentication protocol that allows users to grant third-party applications access to their data without sharing their credentials.
- JWT: A compact, URL-safe means of representing claims to be transferred between two parties, often used for authentication and authorization.
- Basic Authentication: A simple authentication method that requires a username and password to access the API.
What Are the Security Benefits of API Keys?
API keys offer several security benefits, making them a popular choice for authenticating and authorizing access to APIs. Some of the key benefits include:
- Access Control: API keys allow developers to implement fine-grained access controls, specifying which resources or services a particular key can access. This ensures that applications can only perform actions that align with the business logic and security requirements of the organization.
- Usage Monitoring: By requiring API keys for access, developers can track how often an API is being used, by whom, and in what context. This information can help identify trends, optimize performance, and plan for future development.
- Rate Limiting: API keys enable providers to enforce rate limits, preventing abuse and overuse of the system. This helps ensure that resources are allocated efficiently and that the API remains available and responsive to all users.
- Auditability: API keys provide a means of tracking and auditing API usage, helping to identify potential security threats or unauthorized access. This information can be used to improve security measures and protect sensitive data.
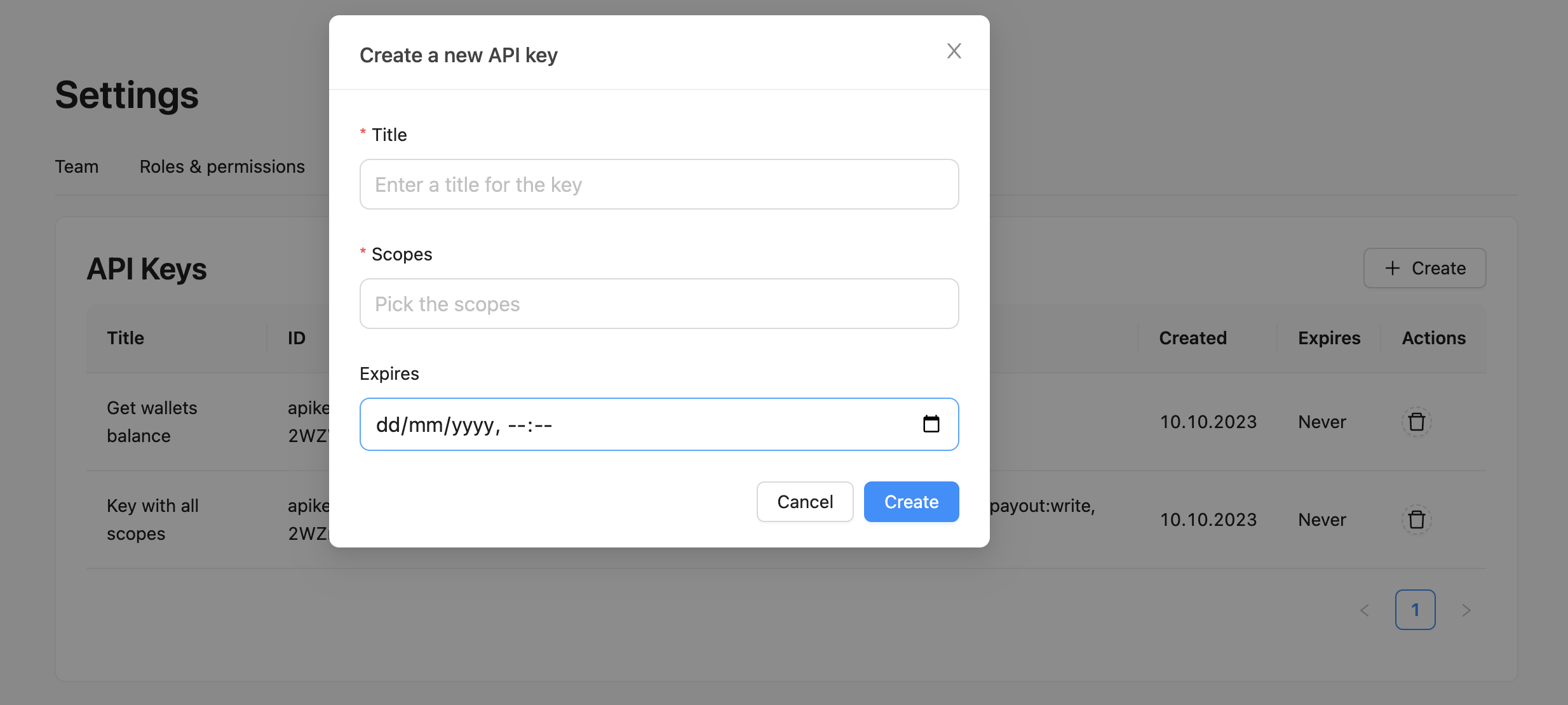
Implementing API Keys in Your Application
Implementing API keys in your application involves several steps, including generating keys, storing them securely, and including them in API requests. Here are some best practices for implementing API keys:
- Generate Strong, Unique Keys: Use a secure method to generate keys that are difficult to guess and unique to each application or user.
- Store Keys Securely: Store keys in a secure location, such as a server-side environment, and never expose them in client-side code or publicly accessible locations.
- Include Keys in API Requests: Include the API key in the request header or as a query parameter when making API calls to authenticate and authorize access to the API.
- Monitor and Rotate Keys Regularly: Regularly monitor API usage and rotate keys to minimize the risk of unauthorized access.
- Implement Access Controls: Use API keys to implement fine-grained access controls, specifying which resources or services a particular key can access.
What Are the Best Practices for Managing API Keys?
Managing API keys effectively is crucial for maintaining the security and performance of your application. Here are some best practices for managing API keys:
- Use Strong, Unique Keys: Generate keys that are difficult to guess and unique to each application or user.
- Store Keys Securely: Store keys in a secure location, such as a server-side environment, and never expose them in client-side code or publicly accessible locations.
- Rotate Keys Regularly: Regularly rotate keys to minimize the risk of unauthorized access.
- Monitor Usage: Track how often an API is being used, by whom, and in what context to identify trends and optimize performance.
- Implement Access Controls: Use API keys to implement fine-grained access controls, specifying which resources or services a particular key can access.
- Enforce Rate Limits: Use API keys to enforce rate limits, preventing abuse and overuse of the system.
Common Challenges with API Keys
While API keys offer several benefits, they also come with challenges that developers must address to ensure the security and performance of their applications. Some common challenges include:
- Key Management: Managing keys effectively can be challenging, particularly for large organizations with many developers and applications. This requires implementing robust processes for generating, storing, and rotating keys.
- Security Risks: Exposing keys in client-side code or publicly accessible locations can pose a security risk, allowing unauthorized parties to gain access to the API.
- Rate Limiting: Enforcing rate limits can be challenging, particularly for applications with high usage volumes or complex access patterns. This requires careful monitoring and optimization to ensure that resources are allocated efficiently.
- Access Controls: Implementing fine-grained access controls can be complex, particularly for APIs with many resources or services. This requires careful planning and testing to ensure that access is granted appropriately.
How to Securely Store API Keys?
Storing API keys securely is crucial for maintaining the security of your application. Here are some best practices for storing API keys:
- Store Keys on the Server-Side: Store keys in a server-side environment, such as a secure database or environment variable, to prevent unauthorized access.
- Encrypt Keys: Use encryption to protect keys from unauthorized access, both at rest and in transit.
- Limit Access: Restrict access to keys to only those who need it, and regularly review access permissions to ensure they are appropriate.
- Rotate Keys Regularly: Regularly rotate keys to minimize the risk of unauthorized access, and update any systems or applications that use the keys.
- Monitor Usage: Track how often keys are being used, by whom, and in what context to identify potential security threats or unauthorized access.
API Keys vs. OAuth Tokens: What's the Difference?
While API keys and OAuth tokens are both methods of authenticating and authorizing access to APIs, they have some key differences that developers should be aware of:
- API Keys: API keys are a simple and effective method of authentication that requires a unique key to access the API. They are typically used for public APIs or when minimal security is needed.
- OAuth Tokens: OAuth tokens are a more complex authentication protocol that allows users to grant third-party applications access to their data without sharing their credentials. They are often used for private APIs or when more robust security is needed.
In general, API keys are best suited for simple use cases where minimal security is needed, while OAuth tokens are more appropriate for complex use cases where robust security is required.
What Are the Limitations of API Keys?
While API keys offer several benefits, they also have limitations that developers should be aware of:
- Limited Security: API keys provide a basic level of security but may not be sufficient for more complex use cases or sensitive data. In these cases, more robust authentication methods, such as OAuth tokens or JWT, may be needed.
- Lack of User Identity: API keys do not provide information about the user or application making the request, making it difficult to implement user-specific access controls or track individual usage patterns.
- Static Nature: API keys are typically static, meaning they do not change over time. This can make it difficult to revoke access or implement dynamic access controls, such as time-based or location-based restrictions.
Future Trends in API Key Management
As the digital landscape continues to evolve, the role of API keys in software development is expected to grow in importance. Some emerging trends in API key management include:
- Increased Security Measures: As cyber threats continue to evolve, developers are likely to implement more robust security measures for API keys, such as encryption, multi-factor authentication, and advanced access controls.
- Automated Key Management: To streamline the process of managing API keys, developers may increasingly rely on automated tools and services that handle key generation, storage, rotation, and monitoring.
- Integration with Identity and Access Management (IAM) Solutions: To provide a more comprehensive approach to security and access control, API keys may increasingly be integrated with IAM solutions, allowing for centralized management and auditing of API access.
Frequently Asked Questions About API Keys
1. What are API keys used for?
API keys are used to authenticate and authorize access to APIs, ensuring that only authorized users or applications can access the resources provided by the API.
2. How are API keys generated?
API keys are typically generated by the API provider and issued to developers who wish to use the API. They are unique to each application or user and must be included in the request header or as a query parameter when making API calls.
3. What are the security benefits of API keys?
API keys offer several security benefits, including access control, usage monitoring, rate limiting, and auditability. They help ensure that only authorized users or applications can access the API, protecting sensitive data and resources from unauthorized access.
4. How can I securely store API keys?
API keys should be stored securely in a server-side environment, such as a secure database or environment variable. They should also be encrypted and access should be limited to only those who need it.
5. What are the limitations of API keys?
API keys provide a basic level of security but may not be sufficient for more complex use cases or sensitive data. They also lack user identity information and are typically static, making it difficult to implement dynamic access controls.
6. How do API keys differ from OAuth tokens?
API keys are a simple method of authentication that requires a unique key to access the API, while OAuth tokens are a more complex authentication protocol that allows users to grant third-party applications access to their data without sharing their credentials.
Conclusion: The Ongoing Role of API Keys
API keys remain a vital component of modern software development, providing a simple and effective means of authenticating and authorizing access to APIs. While they offer several benefits, including security, access control, and usage monitoring, they also have limitations that developers must address to ensure the security and performance of their applications.
As the digital landscape continues to evolve, the role of API keys is expected to grow in importance, with emerging trends in key management, security measures, and integration with identity and access management solutions. By understanding the function and significance of API keys, developers and businesses can harness their power to build secure, interconnected applications that meet the demands of the modern digital world.
For more information on API keys and their role in software development, consider exploring external resources such as ProgrammableWeb's guide on API security.