In the digital age, where information is at our fingertips, understanding the "end to end encrypted meaning" has become increasingly crucial. As our online interactions and data exchanges grow, so does the potential for breaches and unauthorized access. This advanced encryption method ensures that only the communicating users can read the messages, providing a robust layer of security. With the rising concern for digital privacy, end-to-end encryption stands as a beacon of hope, promising confidentiality and peace of mind for users worldwide.
End-to-end encryption is a method of data protection that ensures information is securely transmitted between two devices. This encryption technique prevents unauthorized entities, including service providers, from accessing the data while it's being transferred. The concept of end-to-end encryption is vital in today's digital landscape, where privacy concerns are paramount. By understanding its meaning and implications, individuals and organizations can make informed decisions about their communication and data protection strategies.
In this comprehensive guide, we will explore the "end to end encrypted meaning" in depth, examining its applications, benefits, and challenges. From the basics of how it works to its impact on privacy and security, we will uncover the layers behind this essential digital safeguard. Whether you're a tech enthusiast, a privacy advocate, or simply a curious reader, this article aims to provide valuable insights into the world of end-to-end encryption.
Read also:Breaking News Watch Nick Bosas Viral Hat Video
Table of Contents
- What is End-to-End Encryption?
- How Does End-to-End Encryption Work?
- Why is End-to-End Encryption Important?
- Applications of End-to-End Encryption
- End-to-End Encryption vs. Other Encryption Methods
- Benefits of End-to-End Encryption
- Challenges of Implementing End-to-End Encryption
- Impact on Digital Communication
- Legal and Ethical Considerations
- How to Enable End-to-End Encryption?
- End-to-End Encryption in Messaging Apps
- Future of End-to-End Encryption
- End-to-End Encryption and User Privacy
- Frequently Asked Questions
- Conclusion
What is End-to-End Encryption?
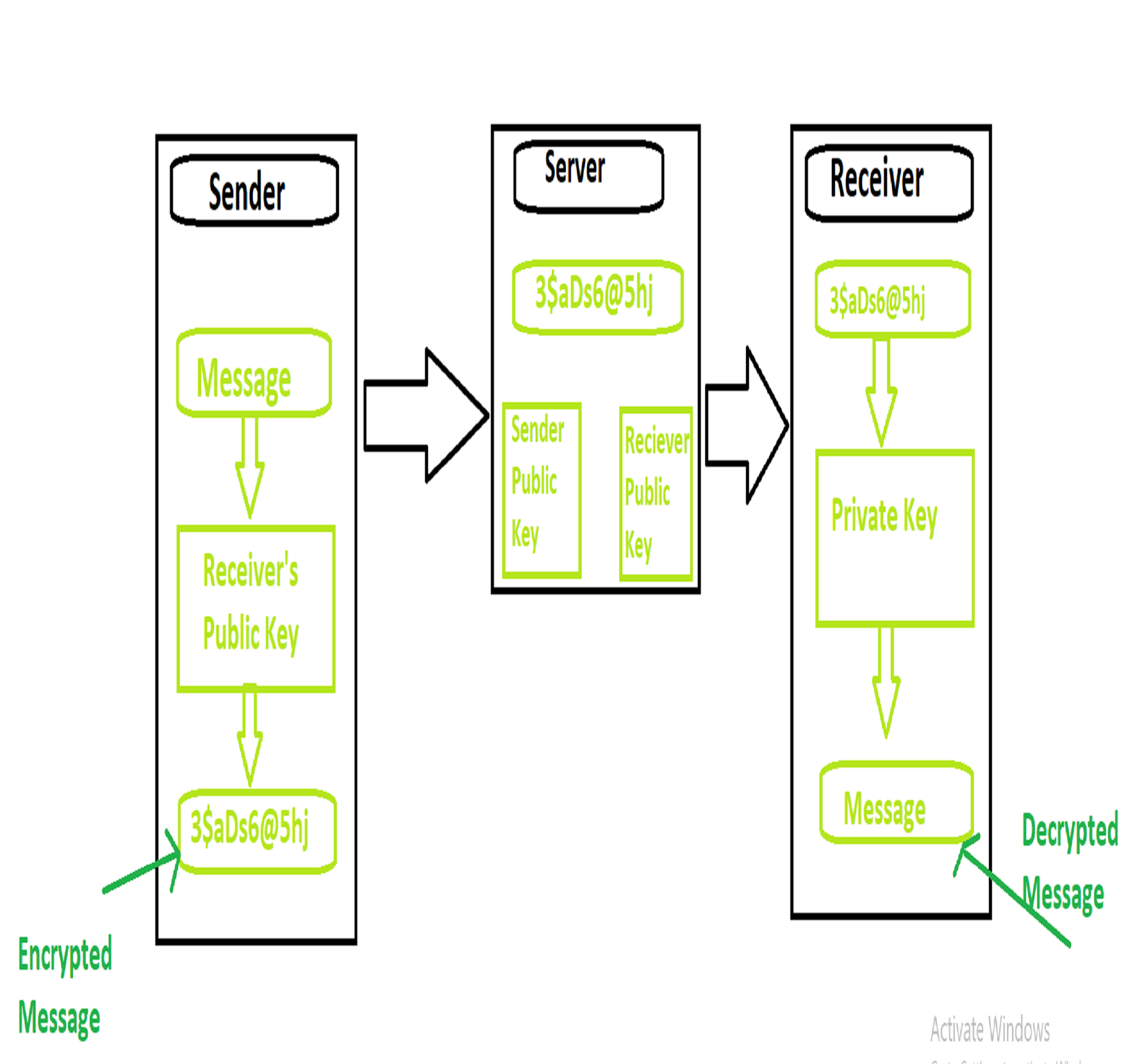
End-to-end encryption (E2EE) is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system or device to another. In this encryption model, only the communicating users can read the messages, ensuring that the data is encrypted on the sender’s device and only decrypted on the recipient’s device. This approach is designed to prevent data from being read or modified by any intermediary nodes, including service providers.
Key Features of End-to-End Encryption
- Data Integrity: Ensures that data is not altered during transmission.
- Confidentiality: Only the intended recipient can decrypt and read the data.
- Authentication: Verifies the identity of the communicating parties.
- Non-repudiation: Ensures that the sender cannot deny sending the message.
Historical Background
The concept of end-to-end encryption has evolved significantly over the years. Initially developed for military and governmental communication, it has now become a standard in various consumer applications, particularly in messaging apps. The rise of digital communication and growing concerns about privacy have accelerated the adoption of end-to-end encryption in the mainstream.
How Does End-to-End Encryption Work?
The process of end-to-end encryption involves several steps to ensure the security of data during transmission. Here's a simplified explanation of how it works:
- Key Generation: Both the sender and recipient generate a pair of cryptographic keys – a public key and a private key. The public key is shared with others, while the private key remains confidential.
- Encryption: The sender uses the recipient's public key to encrypt the message. This ensures that only the recipient can decrypt the message using their private key.
- Transmission: The encrypted message is sent over the network to the recipient.
- Decryption: Upon receiving the message, the recipient uses their private key to decrypt it, making it readable only to them.
Role of Cryptographic Algorithms
Cryptographic algorithms play a crucial role in end-to-end encryption. Advanced algorithms like RSA, AES, and ECC are commonly used to encrypt and decrypt data. These algorithms provide a high level of security by using complex mathematical functions that are computationally difficult to break.
Why is End-to-End Encryption Important?
In an era where digital data is constantly at risk of being intercepted or altered, end-to-end encryption is more important than ever. Here are some of the key reasons why this encryption model is essential:
Protection Against Unauthorized Access
End-to-end encryption ensures that only the intended recipient can access the data, protecting it from unauthorized access by hackers, cybercriminals, and even service providers. This is particularly important for sensitive information, such as personal messages, financial data, and confidential business communications.
Read also:Read The Latest From Bluefield Daily Telegraph
Enhancing User Privacy
By encrypting data from the sender to the recipient, end-to-end encryption enhances user privacy and prevents third parties from analyzing or exploiting the data for commercial or malicious purposes. This level of confidentiality is crucial for maintaining trust in digital communication platforms.
Applications of End-to-End Encryption
End-to-end encryption is applied in various domains to ensure secure communication and data protection. Some of the notable applications include:
Messaging Apps
Popular messaging apps like WhatsApp, Signal, and Telegram utilize end-to-end encryption to secure user messages and calls. This ensures that only the sender and recipient can access the content, protecting it from unauthorized access by the service providers or third parties.
Email Services
Some email services, such as ProtonMail and Tutanota, offer end-to-end encryption to ensure that email communications remain private and secure. This is particularly important for sensitive information exchanged via email, such as legal documents or personal data.
Cloud Storage Services
Cloud storage providers like Tresorit and Sync.com offer end-to-end encryption to protect files stored in the cloud. This ensures that only authorized users can access the content, preventing unauthorized access by service providers or hackers.
End-to-End Encryption vs. Other Encryption Methods
While end-to-end encryption is highly effective in securing communication, it is not the only encryption method available. Here's a comparison of end-to-end encryption with other common encryption methods:
Transport Layer Security (TLS)
TLS is a widely used encryption protocol that secures data in transit between a client and a server. While TLS provides encryption, it does not offer end-to-end encryption, as the data is decrypted at intermediary servers before reaching the recipient.
Encryption at Rest
Encryption at rest protects data stored on devices or servers by encrypting it when it is not being transmitted. While this method ensures data security at rest, it does not provide the same level of protection during transmission as end-to-end encryption.
Comparative Advantages of End-to-End Encryption
- Provides complete data confidentiality during transmission.
- Prevents unauthorized access by service providers.
- Ensures data integrity and authenticity.
Benefits of End-to-End Encryption
End-to-end encryption provides numerous benefits, making it a preferred choice for secure communication. Some of the key benefits include:
High Level of Security
End-to-end encryption offers a high level of security by ensuring that data is encrypted from the sender to the recipient. This prevents unauthorized access and ensures that only the intended recipient can decrypt and read the data.
Data Integrity and Authenticity
By preventing data from being altered during transmission, end-to-end encryption ensures data integrity and authenticity. This is crucial for maintaining trust in digital communication and preventing data tampering or manipulation.
Protection of Sensitive Information
End-to-end encryption is particularly important for protecting sensitive information, such as personal messages, financial data, and confidential business communications. This level of protection is essential for maintaining privacy and preventing data breaches.
Challenges of Implementing End-to-End Encryption
While end-to-end encryption offers significant benefits, it also presents several challenges, including:
Technical Complexity
Implementing end-to-end encryption requires advanced technical expertise and resources. This can be a barrier for organizations with limited technical capabilities or budget constraints.
Legal and Regulatory Concerns
End-to-end encryption can raise legal and regulatory concerns, particularly in regions with strict data protection laws. Organizations must navigate these challenges to ensure compliance while maintaining the security and privacy of their communications.
Limited Access to Data for Service Providers
End-to-end encryption limits access to data for service providers, which can hinder their ability to offer certain services, such as targeted advertising or data analytics. This can impact their business models and revenue streams.
Impact on Digital Communication
End-to-end encryption has a significant impact on digital communication, influencing how data is transmitted and accessed. Some of the key impacts include:
Increased Privacy and Security
End-to-end encryption enhances privacy and security by ensuring that data remains confidential and secure during transmission. This is crucial for maintaining trust in digital communication platforms and preventing data breaches.
Changes in Communication Practices
The adoption of end-to-end encryption has led to changes in communication practices, with users becoming more aware of the importance of privacy and security. This has driven the demand for secure communication platforms and services.
Legal and Ethical Considerations
End-to-end encryption raises several legal and ethical considerations, including:
Balancing Privacy and Security
While end-to-end encryption enhances privacy and security, it can also raise concerns about potential misuse by criminals or terrorists. Governments and organizations must balance the need for privacy with the need for security and law enforcement access.
Compliance with Data Protection Laws
Organizations must ensure compliance with data protection laws and regulations when implementing end-to-end encryption. This includes understanding the legal requirements in different regions and implementing appropriate measures to protect user data.
How to Enable End-to-End Encryption?
Enabling end-to-end encryption involves several steps, depending on the platform or service being used. Here's a general guide to enabling end-to-end encryption:
Choosing a Secure Platform
Select a platform or service that offers end-to-end encryption, such as messaging apps like WhatsApp or Signal. Ensure that the platform provides robust encryption protocols and has a strong reputation for security and privacy.
Activating Encryption Features
Follow the platform's instructions to activate end-to-end encryption features. This may involve updating settings, generating encryption keys, or verifying contacts to ensure secure communication.
End-to-End Encryption in Messaging Apps
Messaging apps are one of the most common applications of end-to-end encryption, providing secure communication for users worldwide. Some of the key features of end-to-end encryption in messaging apps include:
Secure Messaging
End-to-end encryption ensures that messages are securely transmitted between users, preventing unauthorized access by third parties or service providers. This is crucial for maintaining privacy and confidentiality in messaging communications.
Encrypted Voice and Video Calls
Many messaging apps also offer end-to-end encrypted voice and video calls, ensuring that communication remains private and secure. This is particularly important for sensitive or confidential conversations.
Future of End-to-End Encryption
The future of end-to-end encryption is likely to be shaped by advancements in technology and growing concerns about privacy and security. Some of the key trends and developments include:
Advancements in Cryptographic Algorithms
As technology advances, cryptographic algorithms are likely to become more sophisticated and secure, enhancing the effectiveness of end-to-end encryption. This will be crucial for protecting data in an increasingly digital world.
Increased Adoption of Secure Communication Platforms
The demand for secure communication platforms is likely to continue growing, driven by increasing concerns about privacy and security. This will drive the adoption of end-to-end encryption across various communication platforms and services.
End-to-End Encryption and User Privacy
End-to-end encryption plays a crucial role in enhancing user privacy, providing a robust layer of security for digital communication. By preventing unauthorized access to data, end-to-end encryption helps maintain user privacy and trust in digital platforms.
Impact on User Behavior
The adoption of end-to-end encryption has influenced user behavior, with users becoming more aware of the importance of privacy and security. This has driven the demand for secure communication platforms and services, influencing the development of new technologies and solutions.
Building Trust in Digital Platforms
End-to-end encryption is essential for building trust in digital platforms, ensuring that users can communicate securely and confidently. This is crucial for maintaining the integrity and reputation of digital communication platforms and services.
Frequently Asked Questions
What is the main purpose of end-to-end encryption?
The main purpose of end-to-end encryption is to protect data during transmission by ensuring that only the intended recipient can access and read the data. This prevents unauthorized access by third parties, including service providers.
How does end-to-end encryption differ from other encryption methods?
End-to-end encryption differs from other encryption methods by encrypting data from the sender to the recipient, ensuring that only they can access the data. Other encryption methods, such as TLS, may encrypt data in transit but do not provide the same level of protection during transmission.
Can service providers access data protected by end-to-end encryption?
No, service providers cannot access data protected by end-to-end encryption, as it is encrypted from the sender to the recipient. This ensures that only the intended recipient can decrypt and read the data.
What are some common applications of end-to-end encryption?
Common applications of end-to-end encryption include messaging apps, email services, and cloud storage providers. These platforms use end-to-end encryption to secure user communications and data, preventing unauthorized access.
Are there any challenges associated with implementing end-to-end encryption?
Yes, there are several challenges associated with implementing end-to-end encryption, including technical complexity, legal and regulatory concerns, and limited access to data for service providers. Organizations must navigate these challenges to ensure secure and compliant communication.
What is the future of end-to-end encryption?
The future of end-to-end encryption is likely to be shaped by advancements in cryptographic algorithms and growing concerns about privacy and security. This will drive the adoption of secure communication platforms and the development of new technologies and solutions.
Conclusion
In conclusion, understanding the "end to end encrypted meaning" is essential in today's digital world, where privacy and security are paramount. End-to-end encryption offers a robust layer of protection for digital communication, ensuring that data remains confidential and secure during transmission. While there are challenges associated with its implementation, the benefits of end-to-end encryption make it a preferred choice for secure communication across various platforms and services. By enhancing user privacy and trust, end-to-end encryption plays a crucial role in shaping the future of digital communication.
For more information on end-to-end encryption and its applications, consider exploring EFF's Secure Messaging Scorecard, which provides insights into the security features of various communication platforms.